Alex CTF USB Probing 3 – (150)
This write-up is written after reviewing solutions written by other teams. The solutions of these other teams were too short for me to follow in one step. Therefore I would like to write a more extensive write-up of this challenge.
Problem
The challenge consisted of a pcap file of data traffic between the pc and a USB drive.
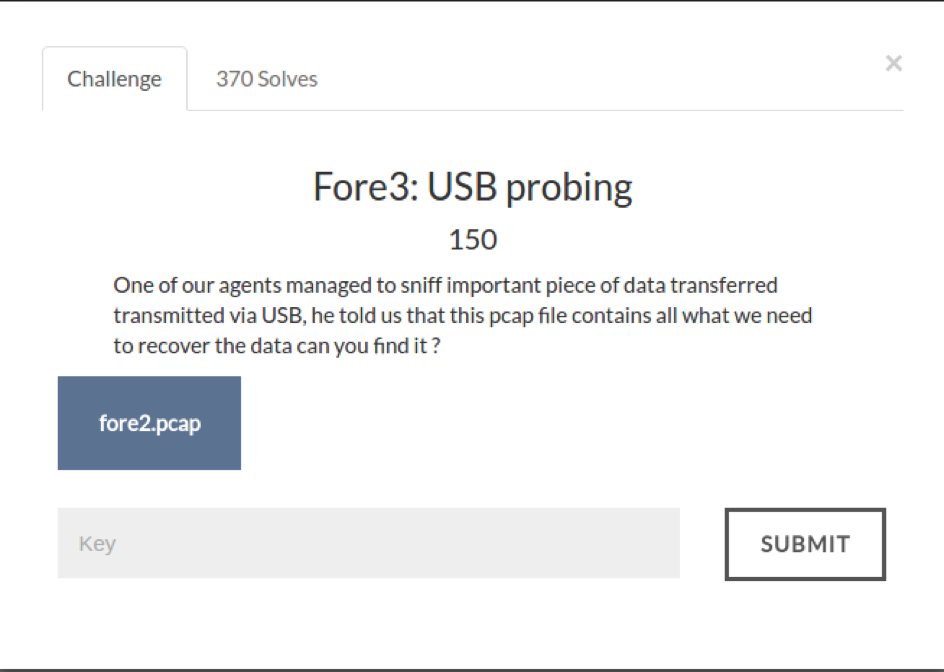 The contents of the pcap file:
The contents of the pcap file:
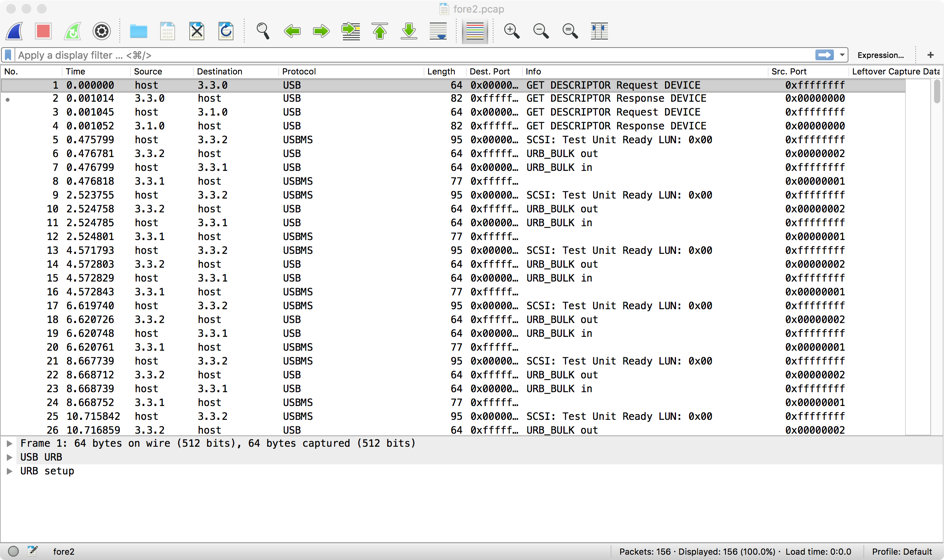
(Unsuccessful) Attempts to solve the problem
- Simply try to export the objects [File ==> Export Objects ==> ]
- After some googling I found a project that could replay the usb traffic to a real USB. I couldn’t get it to work during the CTF. The project sounds really cool and I want to invest some time in the future in order to see if I get this working on my own machine. (https://github.com/wcooley/usbrevue/blob/master/usbreplay.py)
Solution
The pcap file showed 10 files being transferred to the USB drive.
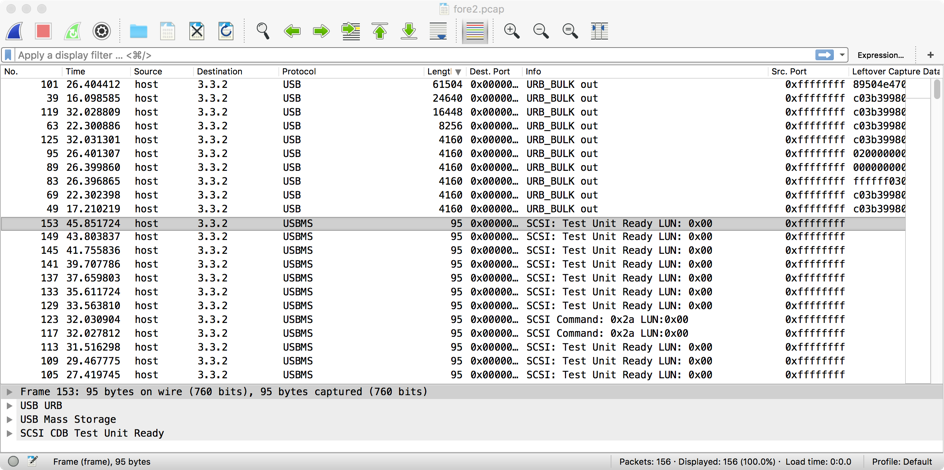 I marked all the URB_BULK out packets [Edit → Mark/Unmark Packet] and exported these marked packets [File → Export Specified Packets …] to the file bulk_out.pcap.
I marked all the URB_BULK out packets [Edit → Mark/Unmark Packet] and exported these marked packets [File → Export Specified Packets …] to the file bulk_out.pcap.
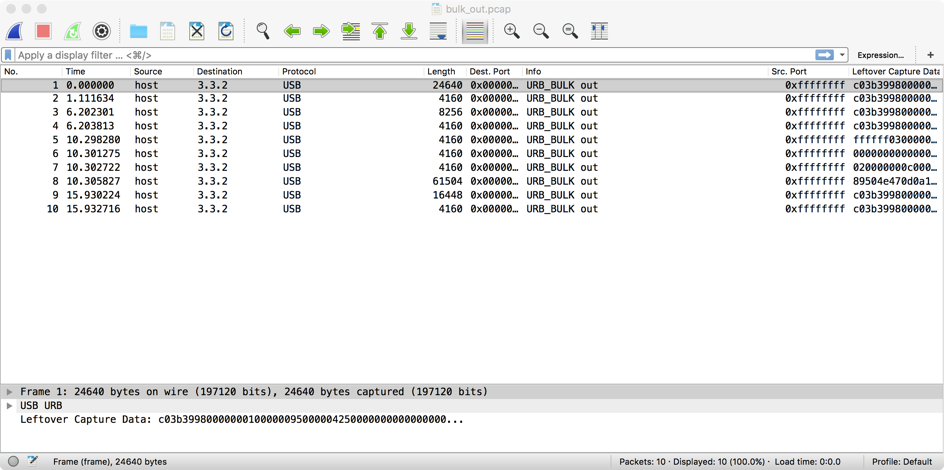 Wireshark didn’t help me by greying out the option to export packet bytes. This is obviously the easiest way to get a file, but I had to write a small script (running on a Mac)
Wireshark didn’t help me by greying out the option to export packet bytes. This is obviously the easiest way to get a file, but I had to write a small script (running on a Mac)
counter=1;
for data in $(tshark -r ./bulk\_out.pcap -T fields -e usb.capdata -Y usb.capdata);
do
echo "$data" | xxd -r -ps > "file$counter.raw"; ((counter++));
done
with the command file file1.raw you can try to let the file system determine the file type. In this case file8.raw gave the following output: file8.raw: PNG image data, 460 x 130, 8-bit/color RGBA, interlaced
This was also visible in Wireshark (it all depends on which route you want to take).
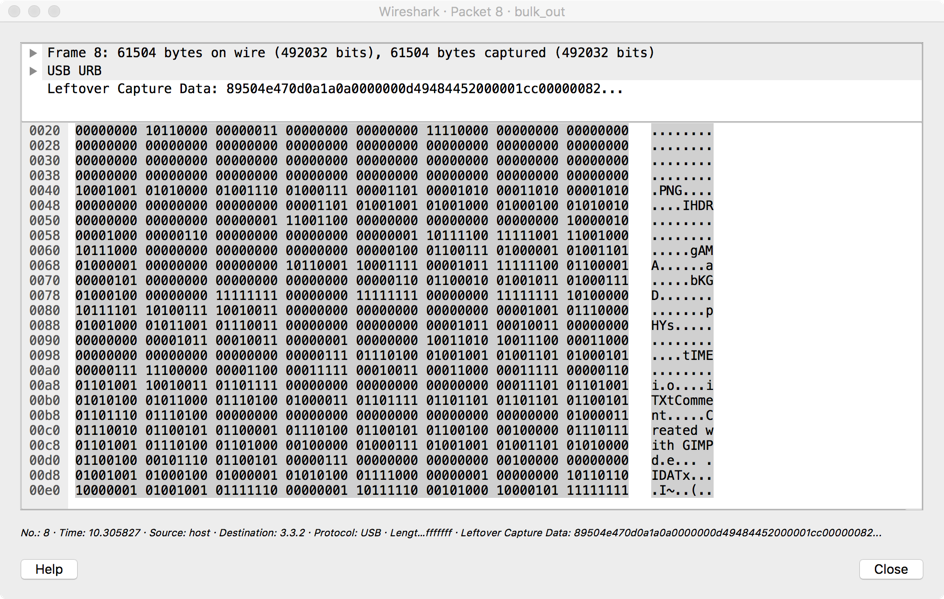 Finally changing the file extension of
Finally changing the file extension of file8.raw to .PNG gave us the result we were waiting for:
